Most people keep a treasure trove of personal information on their phones, from emails and messages on social media to sensitive banking details. As a result, malicious actors often target these devices to compromise your privacy or misuse your identity.

Your sensitive data can entice many people, from those you know to cyber criminals. For this reason, it can be challenging to discover who is behind a phone hack. Still, there are some steps you can take to find out who hacked your phone.
Keep reading to learn more.
How to Find Out Who Hacked Your Phone
Nowadays, most cyberattacks are motivated by monetary gain. During these attacks, hackers typically rely on malware to exploit security vulnerabilities in your operating system or apps you download. After using malware to breach security, they can sell your credentials on the dark web, gain access to your financial accounts or hold your sensitive data for ransom.
In a few extreme cases, your phone can be hacked by someone in your life who wants to monitor your movements and actions or access your private information.
To narrow down your list of suspects, you should determine how your phone was compromised. Here’s what to do.
Check Your App List

Apps are one of the most common vessels for hackers to gain control over your phone. So, you should immediately go through your app list if your device has been acting strangely.
If you spot any apps you don’t remember downloading, you should look them up online and check their reviews. The reviews might mention suspicious activity, confirming the app is the basis for the hack. If you don’t notice any unusual apps, you should run a security scan. Some malware is designed to evade detection, so you might not be able to find it on your own.
Hackers rarely target you personally when infecting your phone with malware. Instead, they’re distributing malware randomly, intending to scrape as much data as possible from as many people as possible. As a result, you won’t have any luck finding out who specifically hacked your phone.
However, if the suspicious app is commercial spyware, chances are you can figure out who is behind the hack. Unfortunately, the app itself won’t be much of a help. These apps usually protect the hacker’s identity by not sending the captured information directly to them. As a result, the details of the individual who installed the spyware aren’t stored anywhere on the infected device.
But, in the case of spyware being installed directly on your smartphone, the hacker has to have physical access to your device. This information can help you create a list of suspects and determine who would benefit from planting spyware on your smartphone. Remember that these apps take little time to install, so consider people who could’ve accessed your phone for a short time.
Check Your Phone Bill

If your phone bill lists charges for texts you’ve never sent, your phone has probably been infected by malware. This type of malware is designed to generate revenue for cybercriminals by forcing your phone to send and receive premium-rate texts.
Unfortunately, you probably won’t be able to figure out precisely who hacked your phone since these attacks are rarely targeted. However, you can stop these charges in one of the following ways:
- Text “STOP” to the unknown number.
- Contact your cell carrier to block the number.

- Run a security app to find and remove malware.

Check Your Call List

If your phone bill and app list don’t reveal anything out of the ordinary, direct your investigation toward your call list. Make sure you haven’t answered any random calls lately since these can be used to hack your information or record your voice.
Again, these attacks are primarily conducted randomly, so you probably won’t be able to pinpoint the exact hacker.
Retrace Your Online Activity

Phishing scams are another common way hackers get access to your private information. Although it’s virtually impossible to guess who’s behind these scams, you can report them to your cell carrier and get them blocked.
While you can’t identify who’s responsible for the attack, you can usually determine whether you’ve fallen victim to phishing. Simply retrace your online activity and check whether you’ve clicked on suspicious links in text messages, emails, or unexpected pop-ups.
These scams typically employ emotional wording, making you click a link for more information without thinking about the potential consequences. So, look for messages containing panic-inducing wording followed by a link.
Consider the Last Time You Used Public Wi-Fi

Both public and password-protected hotspots offer various avenues for people with malicious intent to carry out mass hacking attacks. Suppose your phone has demonstrated issues after you’ve logged into an unsecured public Wi-Fi hotspot. In that case, someone might have scraped your sensitive information.
Check the Safety of Your iCloud Account
If you’re an iPhone user, you should be wary of your iCloud security. After all, a cracked iCloud login can enable anyone to access your photos and plant spyware to monitor your device’s calls, messages, and location.
iCloud accounts with weak passwords and no two-factor authentication can be easily breached by password-cracking software. These programs are used to guess hundreds of common passwords to mass-breach accounts. In other words, they aren’t targeting you personally.
However, weak iCloud security can also let anyone who knows you guess your email and password, especially if you use the same combo across multiple websites.
To determine the culprit, you should contact Apple and ask them to provide details of the access to your account. These details usually contain IP addresses you can use to identify the hacker.
Set a Trap for the Hacker

If you suspect someone’s trying to hack your phone, you can booby-trap it and catch them red-handed. Alternatively, this trap will act as a deterrent and prevent someone from attempting to infiltrate your smartphone.
Apps such as Certo Mobile Security allow iOS and Android users to take a silent photo of the individual trying to hack their phone. This feature will be triggered whenever someone enters an incorrect password multiple times or tries to move the phone.
How to Avoid Getting Hacked Again
After determining who’s responsible for hacking your phone, you should ensure you never have to go through this stressful process again. Being mindful of your digital actions is the way to protect your phone and, thus, your personal information.
Here are some security practices that can help you significantly reduce the chances of getting hacked.
Avoid Downloading Sketchy Apps

Before downloading any app, make sure to comb through the reviews and determine if the app is reputable. If you doubt the app’s safety in the slightest, it’s best not to install it.
Avoid Jailbreaking Your Phone

Jailbreaking allows you to download apps from unofficial app stores. However, it also leaves you vulnerable to getting hacked in two ways.
Firstly, the unofficial apps might be infected with malware or spyware, allowing hackers to access your personal data. Secondly, jailbreaking will stop you from receiving security patches in the latest OS updates, which additionally weakens your phone security.
Keep an Eye on Your Phone at All Times
Physical access is the quickest way for a hacker to compromise your phone. For this reason, keeping your phone on you at all times will keep it safe.
Enable Lost Device Tracking
If you lose track of your phone in public, lost device tracking will be a lifesaver. It will help you locate your phone before it gets stolen or planted with malware. Depending on your device, you might have a native tracking app installed. If not, you can find plenty of third-party apps to add this feature.
Use Phone Security Measures

Even if someone manages to get a hold of your phone, don’t make their job easy. You should always use a passcode lock for your phone. Also, you should never use an easily guessable passcode. This entails your birthday or other important dates and default passwords such as “1234” or “0000.” Ideally, a password should contain letters, numbers, and symbols.
Enable Two-Factor Authentication
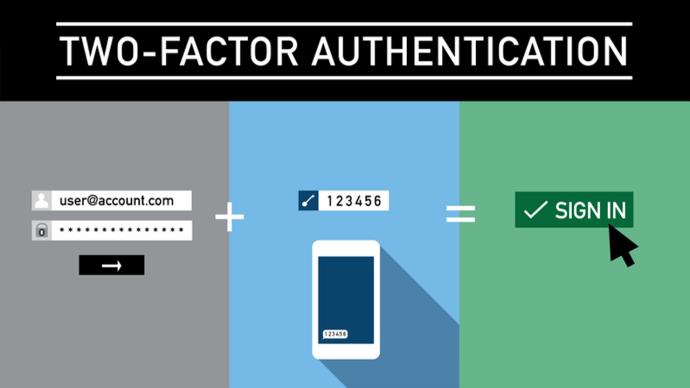
Two-factor authentication adds an additional layer of security to your phone, thus making it harder for hackers to access your device and online accounts.
Depending on your phone, you’ll be able to choose between several options for authentication. The safest option is to use something you physically have, like a USB key, fingerprint, or face ID. Although people frequently use texts and emails for authentication, these can be easily intercepted through hacks like SIM swapping.
Keep All Apps Up to Date

Even trusted apps can be exploited by hackers if not updated regularly. After all, updates usually come with fixes meant to address bugs and security vulnerabilities.
Avoid Using a Public Wi-Fi

You should never log into a public Wi-Fi unless you have virtual private network (VPN) protection. A VPN will encrypt your data so no unwanted viewers can see it.
Stay Vigilant

No one wants unauthorized individuals to look at their personal information, especially with the numerous ways they can misuse this critical data. So, paying attention to mobile security is crucial to protecting your privacy and identity.
Even if you fall victim to a hack, acting fast is essential. Use the methods outlined in this article to figure out who is responsible for the attack. it will be easier to take the necessary steps to remove the threat.
Has your phone ever been hacked? Did you find out who was responsible? Let us know in the comments section below.