In the exciting technological world we live in, everything that has a screen and an internet connection can be hacked into, compromising your security and privacy.

A grim prospect, indeed, but when you take into consideration all the good things that come with the new dawn of technology and social media, you’ll see that the good stuff outweighs the bad stuff by quite a large margin with your Apple iPhone being a prime example of the good stuff.
Aye, it’s things that we can’t possibly go without these days that we’re talking about! Well, you could go without and maybe switch back to a flip phone.
Just imagine: Watching cat videos whenever you like, sharing your vacation photos, finding true love online, as well as uploading some cat videos of your own are only the tip of the iceberg when it comes to the opportunities that come with a mighty online presence!
In this article, we’ll take a closer look at the dark side of Steve’s Job’s greatest invention, the iPhone, and the ubiquitous and incredibly annoying Spyware that plagues these smartphones. But first, I’d like to say, “thanks for all the gadgets, Steve!”
To be precise, we’ll talk about the kinds of infestation there are, and how to spot a cyberattack against your beloved digital companion. (We’re talking about iPhones, NOT Tamagotchis!)
Without further ado, here’s the deal with Spyware and similar nuisances!
Types of iPhone Spyware
First off, ere we proceed with explaining the symptoms of a spyware infestation, let’s take a closer look at the types of these foul online-bound attacks.
Typically, the Spyware takes on one or more of the following three forms:

Masque Attack
Possibly the sneakiest one of the three types of Spyware, a masque attack is a form of spyware infiltration through a well-known and trusted application. Say you use your weather forecast app every day to see if you need to take an umbrella to work or maybe evacuate the city during the hurricane season. A spyware masque attack may look something to this:
- There’s an inviting-looking update for the app,
- Glad to see its attractive new graphics, you rush to install it,
- Boom! Your iPhone’s gone mental all of a sudden!
It really is that simple for your iPhone to succumb to a masque attack, so make sure to check the name of the manufacturer of the update before you install it. If the name sounds dodgy or spammy, chances are- it’s a trap put forth by someone who’s up to no good!
Stay alert while installing and updating anything on your iPhone!
iCloud Backup Attack
Notoriously difficult to detect, iCloud spyware attacks work thus: The hackers figure out your iCloud credentials (password and email) by using specialized spying software.
Once they’re in, they’ll have access to your private information such as texts, call logs, and other sensitive stuff. If you think you may have fallen victim to one of these attacks, try changing your password to shake them off your trail. In case this doesn’t do the trick, contact iCloud support, and report a possible infestation!
Spy App Infestation
When it comes to installing new apps on iPhones, the Apple folks have a pretty stern system of checks and balances which prevents any unverified apps from being available in the app store. Therefore, to get infested with a spy app, you may have done one of these two things:
- Install the suspicious app yourself because you were bored, or
- Get your phone previously hacked. (Then someone else can install the trouble-making apps in your stead.)
If you suspect either of these scenarios is plausible in your case, you can try installing some anti-spyware software such as Certo and then sweeping up the unwanted app.
The Common Symptoms of a Spyware Attack
Given the sneaky nature of spyware attacks, registering the existence of a spy app on your device can be a tough call to make at times.
The symptoms can be many, indeed, but if you keep a watchful eye over your iPhone’s health status, you might be able to tell that something is up if you spot any of the following ‘erratic behaviors’:
- Battery Overheating – Certain pieces of spyware can make your iPhone’s processor overworked thus draining your resources and overheating the battery. If you spot that your battery is constantly getting hot even if you didn’t run any resource-devouring apps, you might be having a spyware problem on your hands that needs to be resolved.
- The Device Connects to Internet Willy-Nilly – If your iPhone mysteriously keeps connecting to the Internet without your knowledge, there’s a possibility a rogue app’s taken control of your device and won’t give up trying to update its foul form into one that is even more awful!
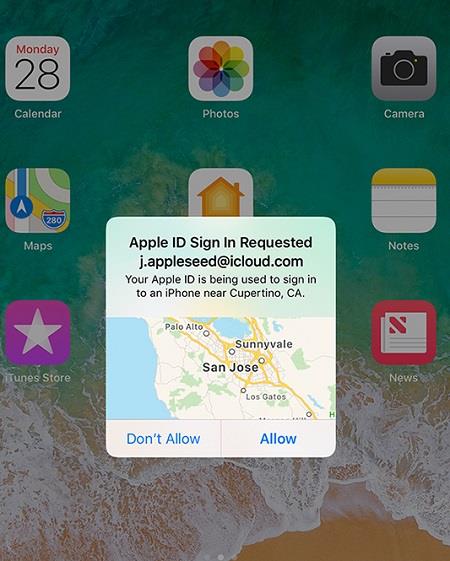
- Apple ID Login Requests – Getting asked to log in constantly even though you were already logged out or have just logged in may also indicate there’s some sort of problem with your device. Most likely, this scenario means someone has taken hold of your password and email address and so they keep logging in when you’re not looking. To combat this, make sure to contact customer support or change your password a bunch of times!
- Unfamiliar Applications – If someone is putting spyware on your phone, they may need to jailbreak it or download an application to your phone. If you do notice an app on your phone that you didn’t download it, research the name of the app, and delete it from your phone.
All in all, no device is immune to an occasional spyware attack, though the good folks at Apple are doing their best to prevent these sorts of attacks.
If you suspect you may have a spyware situation on your iPhone, try not to worry, for there are steps you can take to solve the problem and get back to using your iPhone as normal. We hope you found this article helpful and keep safe with your iPhone ventures!
If you found this article useful, check out other TechJunkie articles, including How To Detect a Hidden Spy Camera with iPhone and How To Check iPhone for Virus.
Do you have any tips, tricks, or just experiences you’d like to tell us about with regard to iPhone security and privacy? If so, please tell us about it in the comments below!