Instructions for creating green ticks for Facebook

Step-by-step guide on how to create a green tick for Facebook. Learn how to verify your account and gain credibility with the green verification mark.
This article will give you a detailed guide on how to use PuTTY on Windows, including how to use a terminal window, configure, create & save profiles, change options and more.
You can download PuTTY for Windows on Download.com.vn and follow the installation instructions like any other software.
If you chose to create the PuTTY icon on the desktop during the installation, simply double-click it to open the program. If not, access PuTTY from the Start menu .
When the software starts, the PuTTY Configuration window will appear. This window has a configuration panel on the left, a Host Name field (or IP address) and other options in the middle, and an active session configuration table at the bottom right.
For simple use, all you need to do is enter the server's domain name or IP address if you want to connect to the Host Name field and click Open (or press Enter ). For example, the domain names students.example.edu, the IP address is of the form 78.99.129.32.
If you don't have a server to connect to, you can use Tectia SSH on Windows or OpenSSH on Linux.
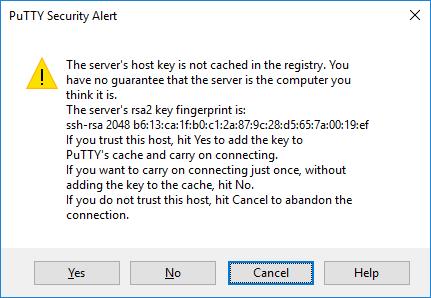
When you connect to the server for the first time, you may see the PuTTY Security Alert dialog box prompting the host server key not to be stored in the registry. This is normal when you first connect to the server. If you've ever received this message on a particular server, it means someone is trying to break the connection and steal your password with an interstitial attack.
As mentioned, this message on the first connection is normal and you just need to click Yes . More carefully, you can check the fingerprint of the displayed key, making sure it is the same server used. In fact, almost no one does that. Instead, they choose the more secure way to use the appropriate SSH Key management solution.
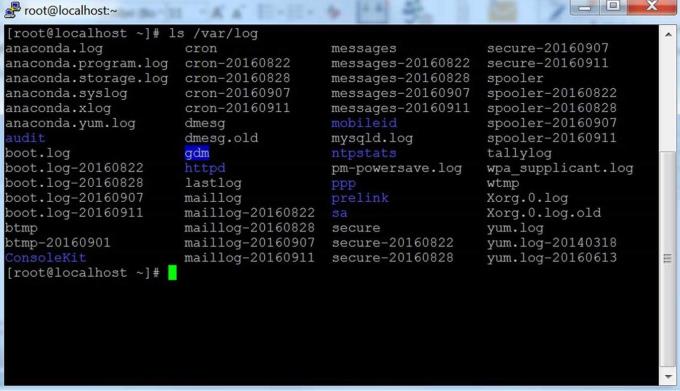
After the security warning, you are taken to a terminal window. By default, it is bland black. First, it asks you to enter your username & password. You will then receive a command line on the server.
Next, you can enter this command into the terminal window. Now that you have connected to the server, everything you type in that window will be sent to this server. All responses from the server are displayed in the terminal window. You can run any text application on the server through that window. The session ends when you exit the command line shell on the server (usually via the exit command or press Control-D ). Alternatively, you can force the session to end by closing the terminal window.
The initial configuration window contains a lot of options. Most of them are not necessary for normal use.
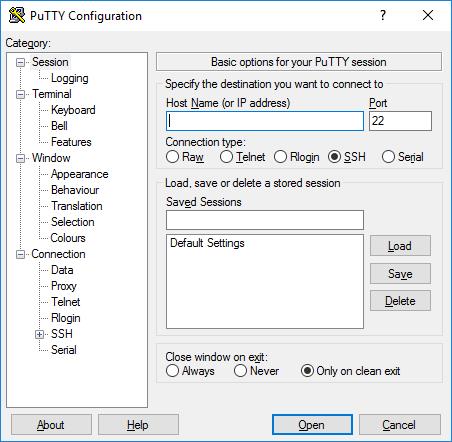
The port field specifies the connected TCP / IP port. For SSH, this is the port the SSH server runs. It usually has a value of 22. If for some reason you need to connect to some other port, just change this value. It is often only the programmer changes it to another value, but this action is also useful for some businesses running SSH servers on non-standard ports or running multiple SSH servers on the same server at different ports. .
You almost never need to change the connection type. Leaving SSH alone is enough because this is a secure encryption protocol designed to ensure passwords & data are protected as much as possible.
Raw connections can be used by a developer to connect a TCP / IP socket to test (for example, when developing a music network application on a TCP / IP port).
Telnet is an old protocol that has almost never been used, unless you manage the device more than 10 years old. Telnet is not secure. The password is sent clearly on the network. Therefore, an attacker can easily eavesdrop on information, stealing username and password. The old Rlogin protocol has similar shortcomings.
Serial or serial ports is another traditional communication mechanism for connecting computers to peripherals. Most computers today no longer use this port, but sometimes they are still used to control physical equipment, musical instruments, machines or communication devices. Serial ports can also be used to debug embedded operating systems or software.
This section allows you to save the settings as a named profile. Just write the new profile name in the Saved Sessions box and click Save to create a new profile. PuTTY stores the server name and other settings in this profile.
The saved profile is now in the larger box below it. Initially, it only contained Default Settings . Your saved profile will be here. Select a profile and click Load to use the previously saved profile. Select a profile and click Delete to delete the profile that is no longer needed.
Finally, the Close window on exit setting specifies how to close the window automatically when the connection is terminated. However, you rarely need to change its default value Only on clean exit .
You can find more options in the Category panel on the left. Select a category here and the right panel will change to display the configuration options for that category. The first options belong to the Session list .
Only relevant options are described here. PuTTY has a lot of other options, but most of them never need to be used.
The options in this catalog affect terminal emulation and keyboard mapping. They are extremely easy to understand so the article is not mentioned here. Very few people need them. Some people may change the way they handle bell characters; Less common operating system users can change the content sent by the spacebar or the Delete character.
These options affect the appearance and behavior of the terminal window. It also specifies how to translate the output characters and selects the font and color for that window.
Data option may be useful when using PuTTY. The auto-login user name will determine the username so you don't have to enter it manually as before. The Proxy option is rarely useful for home users but is essential for businesses that don't allow an Internet connection outside without using a SOCKS proxy or other similar mechanism. Don't worry if you don't know what SOCKS is, just leave this section.
The Telnet , Rlogin and Serial categories only contain options for these protocols. Very few people need to use them.
However, SSH options are important and useful for some people. Ordinary users or students need not worry about them. But if you want to use public key authentication, they are needed. Note that you need to open the SSH option by clicking the [+] icon . If not, you may not see all the available options.
It is almost never necessary to edit these options because all of their defaults are reasonable and most people don't understand coding to make a better choice. So, if you're not sure what to do, skip these options.
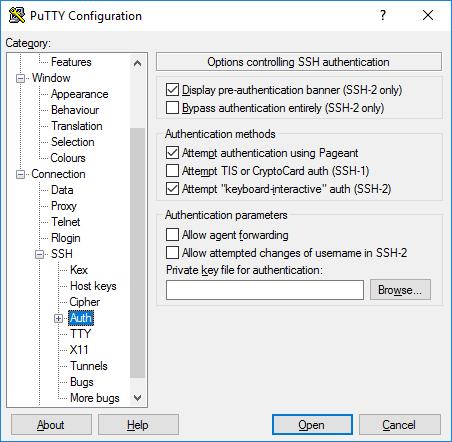
The Auth sub branch contains a number of options that may be helpful. When clicking Auth , it shows the Options controlling SSH authentication panel . To enable public key authentication, simply create the SSH key, then click the Browse button in the Authentication parameters box located in the middle right of the configuration panel. Advanced users can check the Allow agent forwarding box to log in using a one-time key.
Most users do not need to create an SSH Key and understand the meaning of public key authentication. However, system administrators need to know and be familiar with managing SSH Key and at the same time, ensure that the organization implements the provisioning & termination processes and verifies the appropriate SSH Key.
One of the interesting features of PuTTY is the one-time login to Active Directory. In theory, it uses the Kerberos protocol via the GSSAPI programming interface. In the SSH protocol, this mechanism is called GSSAPI authentication. Business users who use Kerberos authentication (for example, through Centrify or Quest Authentication Services or Vintela) may want to take advantage of this one-time login feature. Other users don't care about it. GSSAPI authentication settings can be found in the SSH / Auth section. Note, you must expand the Auth section again by clicking the [+] icon to see the GSSAPI options.
X11 is a protocol and system that runs graphical applications on Unix and Linux. It supports running graphical applications remotely via external networks.
PuTTY does not deploy the X11 server (display side), but it may work with some products running the X server feature on Windows. XMing is a popular free alternative.
To use the X11 server, you need to check the Enable X11 forwarding box and enter localhost: 0.0 in the X display location box . No need to adjust other settings.
These options are used to configure SSH tunneling, also known as SSH port forwarding. This table can be used to determine connection forwarding. Forwarding operations are saved in profiles.
To add local forwarding (for example, forwarding the TCP / IP port on the local machine to the port on the remote device or to a remote connected machine), write the source port into the Source port field , the destination server. and port (e.g. www.dest.com:80) in the Destination field and select Local . Click Add .
To add remote forwarding (for example, forwarding the TCP / IP port on the remote computer to the port on the local computer or device that the local machine can access), select Source port on the destination computer and Destination as the device. accessible from local machine.
Normally, you do not need to check local ports accept connection from server or similar for remote ports. However, if the connection to the port is forwarded from the network instead of localhost, you need to check them. Although there is a small security risk, it is not a problem in the case of SSH tunneling . However, you need to understand that anyone who can connect to the corresponding computer is able to connect to that forwarded port. In some cases, you can use port forwarding to bypass firewalls.
Above is how to use PuTTY basic on Windows . Hope the article is helpful to you.
Step-by-step guide on how to create a green tick for Facebook. Learn how to verify your account and gain credibility with the green verification mark.
Learn how to download torrent files directly using the Firefox web browser with the Torrent Tornado add-on. Simple steps for effective torrent downloading.
Learn how to view someone else’s TikTok followers, both on public and private accounts. Discover effective methods to access follower counts and improve your TikTok strategy.
Learn how to login to Facebook using your email, phone number, or even QR Code authentication without entering a password.
Learn how to stop echo during your Parsec streaming sessions with effective solutions. Echo is a common issue that disrupts communication in games, and we provide proven methods to eliminate it.
Discover how to change your avatar and cover photo on Zalo to express your personality. Follow our easy guide and optimize your Zalo profile image.
Learn how to manage your relationships on Zalo by marking close friends, similar to Instagram. This feature allows easy access to frequently contacted individuals.
Learn how to send screenshots via Viber quickly and without saving them. This guide provides step-by-step instructions to enhance your messaging experience.
Learn how to easily restore deleted messages on Zalo with our step-by-step instructions. Quickly recover your important chats on this popular messaging app.
Discover how to easily add background music to your personal Zalo page with our comprehensive guide on using Zalo for Android and iOS devices.
If you’ve ever found yourself at the end of a Minecraft raid, searching for the last raider to eliminate, you’re not alone. Many players have faced this challenge.
Learn how to uninstall Coc Coc browser completely from your computer, ensuring all data is removed. Follow these simple steps for an effective uninstallation.
Discover how to effectively use the Toshiba AW-A800SV washing machine control panel with our detailed guide!
Discover how to effectively use emergency features on Samsung Galaxy Watch and other smartwatches, including SOS alerts, fall detection, and health records.
Discover how to effectively <strong>share QR code on Zalo</strong>. QR codes enhance connectivity, enabling easy friend requests and more on Zalo.













