How to pin comments on TikTok

How to pin comments on TikTok, TikTok allows users to pin comments easily. Here's how to pin comments on TikTok videos.
In the exciting technological world we live in, everything that has a screen and an internet connection can be hacked into, compromising your security and privacy.

A grim prospect, indeed, but when you take into consideration all the good things that come with the new dawn of technology and social media, you’ll see that the good stuff outweighs the bad stuff by quite a large margin with your Apple iPhone being a prime example of the good stuff.
Aye, it’s things that we can’t possibly go without these days that we’re talking about! Well, you could go without and maybe switch back to a flip phone.
Just imagine: Watching cat videos whenever you like, sharing your vacation photos, finding true love online, as well as uploading some cat videos of your own are only the tip of the iceberg when it comes to the opportunities that come with a mighty online presence!
In this article, we’ll take a closer look at the dark side of Steve’s Job’s greatest invention, the iPhone, and the ubiquitous and incredibly annoying Spyware that plagues these smartphones. But first, I’d like to say, “thanks for all the gadgets, Steve!”
To be precise, we’ll talk about the kinds of infestation there are, and how to spot a cyberattack against your beloved digital companion. (We’re talking about iPhones, NOT Tamagotchis!)
Without further ado, here’s the deal with Spyware and similar nuisances!
Types of iPhone Spyware
First off, ere we proceed with explaining the symptoms of a spyware infestation, let’s take a closer look at the types of these foul online-bound attacks.
Typically, the Spyware takes on one or more of the following three forms:

Masque Attack
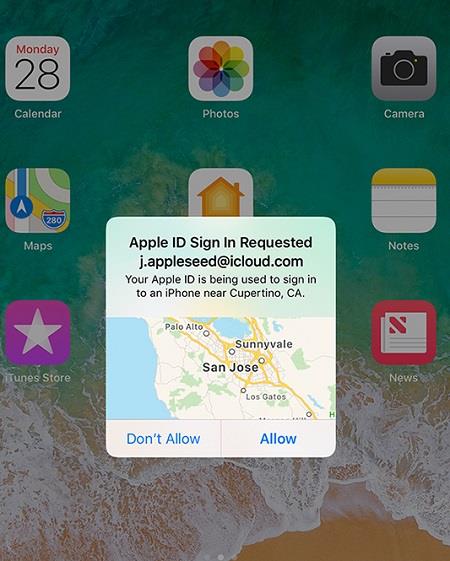
Possibly the sneakiest one of the three types of Spyware, a masque attack is a form of spyware infiltration through a well-known and trusted application. Say you use your weather forecast app every day to see if you need to take an umbrella to work or maybe evacuate the city during the hurricane season. A spyware masque attack may look something to this:
It really is that simple for your iPhone to succumb to a masque attack, so make sure to check the name of the manufacturer of the update before you install it. If the name sounds dodgy or spammy, chances are- it’s a trap put forth by someone who’s up to no good!
Stay alert while installing and updating anything on your iPhone!
iCloud Backup Attack
Notoriously difficult to detect, iCloud spyware attacks work thus: The hackers figure out your iCloud credentials (password and email) by using specialized spying software.
Once they’re in, they’ll have access to your private information such as texts, call logs, and other sensitive stuff. If you think you may have fallen victim to one of these attacks, try changing your password to shake them off your trail. In case this doesn’t do the trick, contact iCloud support, and report a possible infestation!
Spy App Infestation
When it comes to installing new apps on iPhones, the Apple folks have a pretty stern system of checks and balances which prevents any unverified apps from being available in the app store. Therefore, to get infested with a spy app, you may have done one of these two things:
If you suspect either of these scenarios is plausible in your case, you can try installing some anti-spyware software such as Certo and then sweeping up the unwanted app.
The Common Symptoms of a Spyware Attack
Given the sneaky nature of spyware attacks, registering the existence of a spy app on your device can be a tough call to make at times.
The symptoms can be many, indeed, but if you keep a watchful eye over your iPhone’s health status, you might be able to tell that something is up if you spot any of the following ‘erratic behaviors’:
All in all, no device is immune to an occasional spyware attack, though the good folks at Apple are doing their best to prevent these sorts of attacks.
If you suspect you may have a spyware situation on your iPhone, try not to worry, for there are steps you can take to solve the problem and get back to using your iPhone as normal. We hope you found this article helpful and keep safe with your iPhone ventures!
If you found this article useful, check out other TechJunkie articles, including How To Detect a Hidden Spy Camera with iPhone and How To Check iPhone for Virus.
Do you have any tips, tricks, or just experiences you’d like to tell us about with regard to iPhone security and privacy? If so, please tell us about it in the comments below!
How to pin comments on TikTok, TikTok allows users to pin comments easily. Here's how to pin comments on TikTok videos.
Instructions for Organizing a Q&A session on Facebook, Recently, Facebook has launched the feature to create a Q&A session, when you post a question for everyone to answer.
Instructions for installing and recording videos with Likee, Likee is an application that supports extremely beautiful and impressive video recording, and is loved by many young people today. The following,
How to export the list of meeting participants in Zoom, How to take attendance on Zoom is not difficult, it even allows you to export the list of students participating in the class.
How to change font on Xiaomi, Want to create a new image for Xiaomi device? Just follow the instructions below to change the font style and size above
Instructions for creating a mirror image effect on Picsart, Picsart is an application where users only need to perform a few simple steps to transform the photo.
How to add new fonts to Microsoft Word, Can't find the font you want to use for documents in Microsoft Word? Don't worry, you can install new fonts for Word according to these steps
How to turn off the computer screen and still have the computer running, How to turn off the PC screen and still have the computer running on Win 10/11? Very simple. Here's how to turn off the computer screen
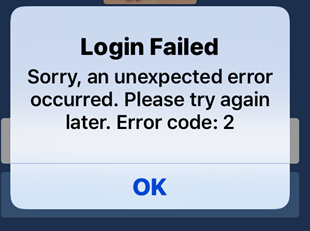
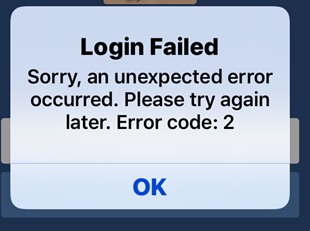
To fix the “An unexpected error occurred” issue when logging in to Facebook, you can try the following steps
Users reported that their Facebook, Messenger and Instagram accounts were suddenly logged out and could not be accessed again, both on the app and web version.
Instructions on how to take photos on Tiktok are extremely simple. Tiktok is a famous application for recording and creating short videos on social networks. However, this application also
How to find and get Instagram links, Instagram is one of the most popular and easy-to-use social networking platforms today. However, because it is designed specifically for mobile,
Instructions for locking the mouse cursor when playing games on BlueStacks, Instructions for turning on/off the mouse cursor lock feature when playing games in the BlueStacks App Player emulator.
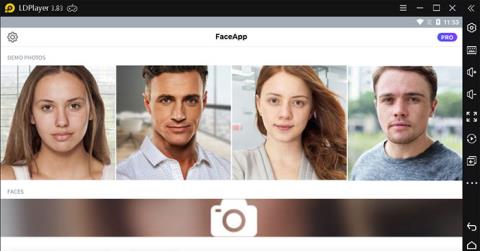
Instructions for installing and using Faceapp using an emulator on PC, Simple and easy instructions on how to install and use the Faceapp face editing app using an emulator on PC
Instructions for creating a cover photo group on Facebook, Creating a cover photo group is a feature that helps users set Facebook cover photos with many different images (maximum of 6 photos).
Learn how to effectively use the Stochastic Indicator for technical analysis on Bubinga. Explore advanced techniques to enhance your trading strategies
Instructions for adding angel wings to photos using PicsArt, PicsArt is a photo editing application used by many people today. Today WebTech360 will introduce the article
How to turn off the Just accessed notification on Zalo. This article WebTech360 will guide you to turn off the Just accessed notification under your Zalo chat name.
Instructions for blocking and unblocking accounts on TikTok. Similar to other social networking applications, TikTok also allows users to block someone's account
How to write a long status with a colorful background on Facebook, Today, WebTech360 will introduce some steps to post a long status with a colorful background on Facebook,