How to Create Pixar Style Characters with ChatGPT
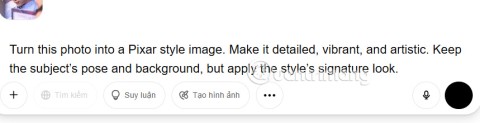
Following the trend of creating unique Ghibli style art and toy action figures, in this article you will be guided to create Pixar style characters.
In today's world, USB portable storage devices are an essential part of our daily lives. They are compact, affordable, and highly efficient for sharing data in workplaces, schools, and various environments. However, these devices also pose significant risks owing to the potential spread of viruses. Among the many solutions to mitigate this risk, iKill stands out as a powerful tool.
USB devices such as flash drives, iPods, mp3 players, and cell phones can carry malware along with data. When a user connects these devices to a computer, any double-click on the device could automatically execute a virus thanks to the autorun.inf file. Malicious software can also hide during standard operations, resulting in severe infections.
To mitigate the dangers posed by viruses, mere vigilance is insufficient. In this light, leveraging robust software tools like iKill is paramount.
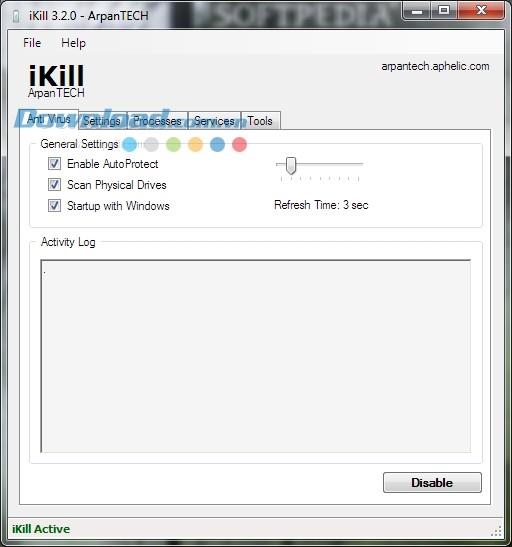
iKill operates through a device scanning mechanism that activates as soon as USB devices are connected. It scans the autorun.inf file to determine if it is safe to run. When AutoProtect is enabled, it automatically deletes any potentially harmful files found on the device. If AutoProtect is disabled, the program prompts the user about deleting threatening files.
| Process | Description |
|---|---|
| Scanning | iKill scans the USB device for autorun.inf files whenever connected. |
| File Deletion | Automatically deletes harmful files with AutoProtect or prompts for user action. |
| User Consent | When a harmful file is detected, it asks for the user’s confirmation to delete it. |
After detecting the autorun.inf, iKill seeks user approval to delete any executable files. The program ensures that no autorun.inf file remains on the USB device, which is a unique and valuable feature compared to similar applications.
In conjunction with iKill, users may find the following tools beneficial for enhancing data security:
Following the trend of creating unique Ghibli style art and toy action figures, in this article you will be guided to create Pixar style characters.
Code Fantasy of Light gives players a series of attractive rewards, including gold coins and Purple Crystals for you to use.
In general, Infinity Squad DTCL, like many other squads, cannot evaluate many combinations because there are not many BĐVC squads tested. However, this will probably be the most popular clan in the upcoming Infinity Squad.
Dishwashing liquid can be made at home if you are not sure about the quality of products on the market. Below are detailed instructions on how to make dishwashing liquid at home.
Procrastination is not just a bad habit, it's a way of life that some people spend years trying to break. Everyone wants to be more productive, but it's not easy.
Using a computer security key is the best way to authenticate your identity, but not all security keys are created equal. USB, NFC, and Bluetooth security keys all have their own advantages and disadvantages.
Even if you no longer use your old device, you should keep it registered on Find My Device for the following reasons.
Apple has just announced a much-anticipated feature on iOS 18.1 that brings joy to iPhone and iPad users, which is the ability to change iCloud email address.
Now, research has proven this theory, illustrating that changing passwords frequently leads to security problems.
The universe is an almost absolute vacuum. Why is that? Let's learn about the vacuum of the universe together!
Whether real shipwrecks or ghostly phenomena, these ships carry tales of unexplained deaths, flying orbs, and screams from the depths of the sea.
Recently, NASA has released many clear images of different regions in the universe taken by the world's largest telescope, James Webb.
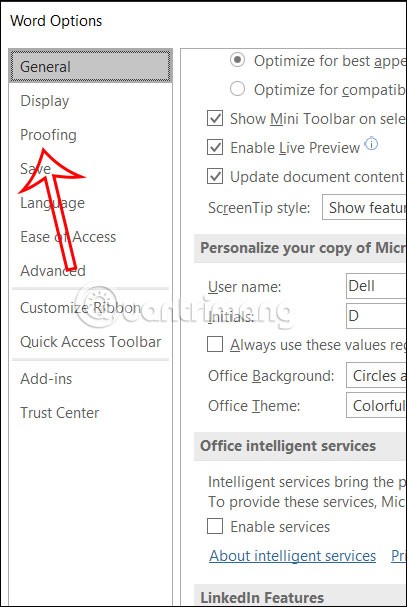
With their own custom dictionary in Word, users can easily enter content without being prompted for misspellings with special words.
Gangs are back in the TFT season 14 meta in a different form than before, but still featuring familiar faces like Twisted Fate, Braum, and Shaco.
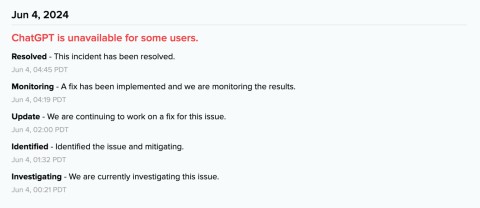
According to OpenAI's system status page, ChatGPT is currently down for a small group of users, many of whom are unable to use the Android mobile app or other services.