How to Detect and Mitigate Botnet Attacks
Botnet attacks are one of the most serious cybersecurity threats today.
If physical warfare is fought with armies, digital warfare is won with infected botnet devices. The more infected devices in a botnet, the more powerful the attacks. A recent campaign set a record for the most powerful DDoS attack in history, generating 5.6 Tbps of data in a single session.
Cloudflare Puts Up an Incredible Fight Against Record-Breaking DDoS Attack
The announcement comes from cybersecurity company Cloudflare, which provides website owners with protection against DDoS attacks and defenses against everyday attacks. Chances are, if you've ever clicked on the "Are you human?" CAPTCHA test, Cloudflare is the company that provided it.
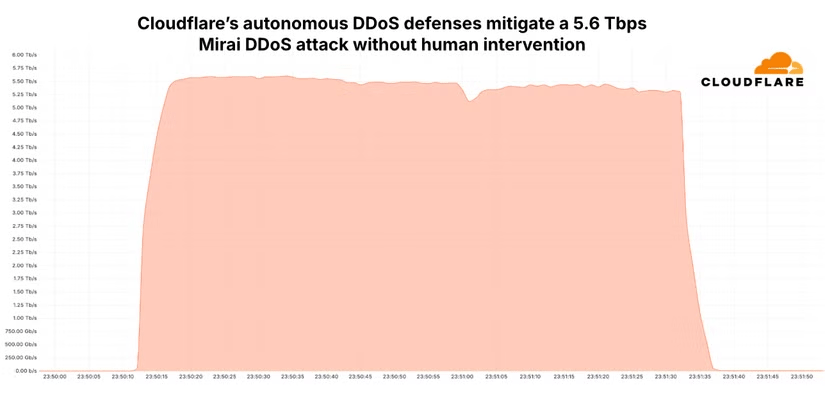
In a blog post by Cloudflare, the cybersecurity company analyzed the most intense DDoS attack in recorded history:
On October 29, a 5.6 Tbps UDP DDoS attack launched by a Mirai variant botnet targeted a customer of Cloudflare Magic Transit, an Internet Service Provider (ISP) in East Asia. The attack lasted just 80 seconds and originated from over 13,000 IoT devices. Detection and mitigation were fully automated thanks to Cloudflare’s distributed defense systems. It did not require human intervention, did not trigger any alerts, and did not cause any performance degradation. Systems continued to operate as normal.
It’s good to have companies like Cloudflare there to protect websites, as botnet operators have been ramping up their activity recently. Cloudflare reports that it began seeing a spike in DDoS attacks in Q3 2024, and by Q4 2024, the company saw an 1,885% quarter-over-quarter increase in attacks using more than 1Tbps of traffic.
The strength of a botnet is determined by the number of devices it has taken control of, so now is the perfect time to make sure cybercriminals don’t include your gadgets in the next big attack. Check out how to detect and mitigate botnet attacks for more information, and if you have a lot of smart devices, be sure to learn about IoT botnets too!
What is Firmware? How is Firmware different from Software? Let's find out with WebTech360 in this article!
Imagine being able to instantly find any file on your computer with just a few keystrokes! File Explorer offers powerful search tricks that make locating files a breeze.

If you have a smart home, chances are you already use an assistant like Alexa, Google Assistant, or Siri. But do these popular home assistants use AI to work, and if so, how?
If you see the message “There was a problem resetting your PC. No changes were made”, “Can't reset your PC”, or “There was a problem refreshing your PC”, you won't be able to restore your PC to its factory defaults.
Apple Podcasts is now available on desktop browsers, including Firefox, Chrome, Edge, and Safari. Just sign in to your Apple account to listen to podcasts and follow your favorite podcast channels.
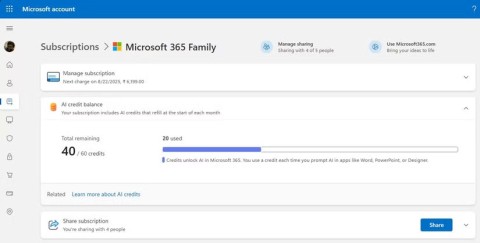
Microsoft now offers AI-powered Copilot features as part of existing Microsoft 365 Personal and Family subscriptions—no add-on required. But the capabilities aren't limitless—they work on a new system called AI credits.
You will get recruitment tickets, breakthrough stones, gold and even 5-star SSR characters in Code Tien Len Alita.
The Peroxide Codes given to players are mostly amounts of Product Essence that are used frequently in the game.

Hack Spin Coin Master, Hack Coin Master Spins is the method that many Coin Master players use if they want to get a large number of spins.

If you have cleaned your oven or microwave with detergent, you can deodorize it with super cheap and super easy-to-find ingredients in our article!

After a period of use, the washing machine will continuously drain water. Please refer to this article of ours to find out the cause and how to fix it!
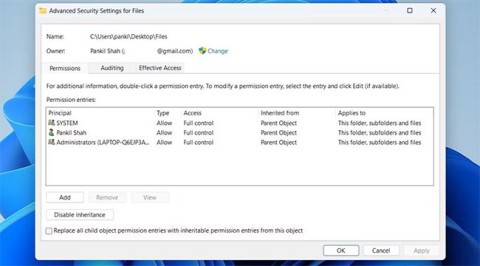
When Windows displays the error “You don't have permission to save in this location”, this will prevent you from saving files to the desired folders.
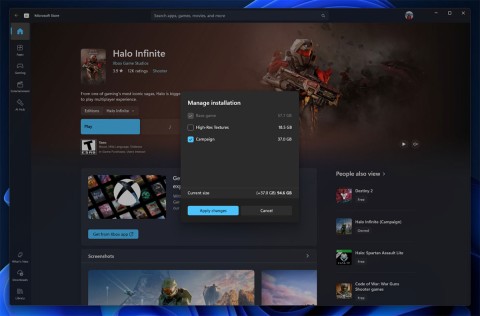
Recently, in addition to releasing Windows 11 Canary build 27788, Microsoft also released a new update for the Microsoft Store app on the test channels of the Windows Insiders program.

When it comes to cable TV, people often spend more time flipping through channels than actually watching it. Many people have been off cable for years and have never looked back.
This malware infects people looking to avoid paying for the product, steals their personal information, and turns their computers into cryptocurrency mining zombies.