They are advantages and disadvantages with the advent of technology being used in almost every angle of day-to-day lives. Technology has brought in a lot of ease in our operations at home, our offices, and businesses as well. Through the use of technology, organizations, business entities, and manufacturing industries can automate their operations such that there needs to be no physical manpower for a task to be done.
There are also disadvantages of technology in that it can fail and disrupt all the operations that relied on it. Some people have ill motives in the online space. These people are there to steal, alter or destroy someone’s, an organization’s, business entities, and manufacturing industry’s information. They do this with the motive that they will not accomplish what they had planned to do.
People that love the content on the internet will often use a Virtual Private Network to access what has been restricted in their countries. For movie and series lovers, it is through here you can find how to watch Netflix using VPN and get no restrictions on what kind of movies or series to watch. However, VPN users should always be on the lookout for online hackers who come through different ways.
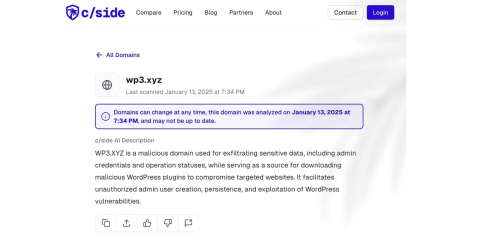
Online users can get access to a computer system with no authorization. They do this by installing malware on people, organizations, business entities, and manufacturing industries' computers and computer systems. Malware is hence defined as software that brings harm to a computer, computer system, or the files saved in a computer.

7 Types of Malware Attacks and How to Prevent Them
There are numerous types of Malware attacks. This article will highlight seven types of Malware attacks and how they can be prevented.
Adware
The adware malware attack displays themselves as pop ads as a computer user is surfing the internet. If a computer user clicks on these pop ads, they immediately take you to other sites that help hackers gain access to your computer device.
Virus
Virus malware attacks come hand in hand with the formats in which one saves their computer files. It is hence important for computer users to be careful about the kind of files they download and the formats in which they save their computer files.
Worm
Another type of Malware attack is a worm that an online hacker installs in computers and computer systems. A worm is also capable of getting access to your data and being able to steal it and giving easy access to your computer and computer system to online hackers. The worm has the capability of slowing the internet bandwidth a computer user could be using for his or her internet connectivity.
A worm malware attack is also capable of giving online hackers backdoor access to a computer device. Once a worm has access to a personal computer or computer system, it is capable of spreading in all parts of a computer and deteriorating the functions of the machine. One of the major disruptions that a worm can bring to a computer or a computer system is deleting the files you have saved.
Computers users could restrict the worm malware attack from invading their computer devices and systems by limiting or giving restrictions to the number of people that visit their websites at a go.
Trojan Horse
A trojan horse is a malware attack that looks like a valid file to a computer user. It hence makes it easy for a hacker to get access to a computer device or computer system because a computer user will hardly suspect it as a file that ought not to be in his or her computer. A trojan horse malware attack can easily spy on your computer device, get access to your internet network and consequently delete and gain access to the data you have saved on your computer.
Spyware
The spyware malware attack gets installed in one’s computer or computer system through pop-up ads and online activities that happen with a computer user’s knowledge. Through the spyware malware attack, hackers gain access to a computer user’s passwords and get acquainted with all the sites one visits oftentimes.
Ransomware
The ransomware malware attacks come in two forms the Crypto and locker ransomware. This means that hackers give themselves the power of web administrators. They can hence control who accesses their computer systems and have the capability of deleting files or data.
When a ransomware malware attack is installed in your computer device or computer system by an online hacker, a computer user can hardly get access to his files or easily use his or her computer. This hence prompts a computer user to make a payment to get back access to his or her computer files and be able to use his or her computing device. If a computer user falls into the trap and attempts to make a payment, they could easily lose all their data.
However, a computer user can avoid ransomware by changing the passwords of their website administrators oftentimes and being aware of any discrepancies that may be occurring in their files or computer systems.
Phishing
The phishing malware attack gains access to a person, organization, business entity, or manufacturing industry’s computer when a computer user opens emails sent to them. Some emails sent seemingly look like they are from trusted sources but they are not. These emails could be inquiring about personal details such as bank details. A computer user could easily dish out their information and eventually have their data stolen.
Ways to Prevent Malware Attacks
- Use secure passwords especially those that are not easy to guess.
- Always update your computer software
- Avoid pop up ads
- Avoid opening emails sent in from unknown email addresses
- Educate your organization’s computer users of ways they could detect malware attacks and how to avoid them
- Update your computer systems oftentimes
- Install a trusted antivirus on your computer device
- Beware of unknown downloads and files saved on your computer device
Conclusion
It is key that computer users, organizations, business entities, and manufacturing industries that use computers be keen on their online presence. Online hackers are always on the watch and it is up to computer users to safeguard their passwords and avoid clicking on any pop-up or emails that look suspicious.